As the year ends, Security magazine spotlights cybersecurity solutions released in 2022. Covering everything from insider risk mitigation to improved threat monitoring, we spotlight innovative cybersecurity products and technology that can help enterprise security teams build successful programs.
Blumira
Enables Security Information & Event Management
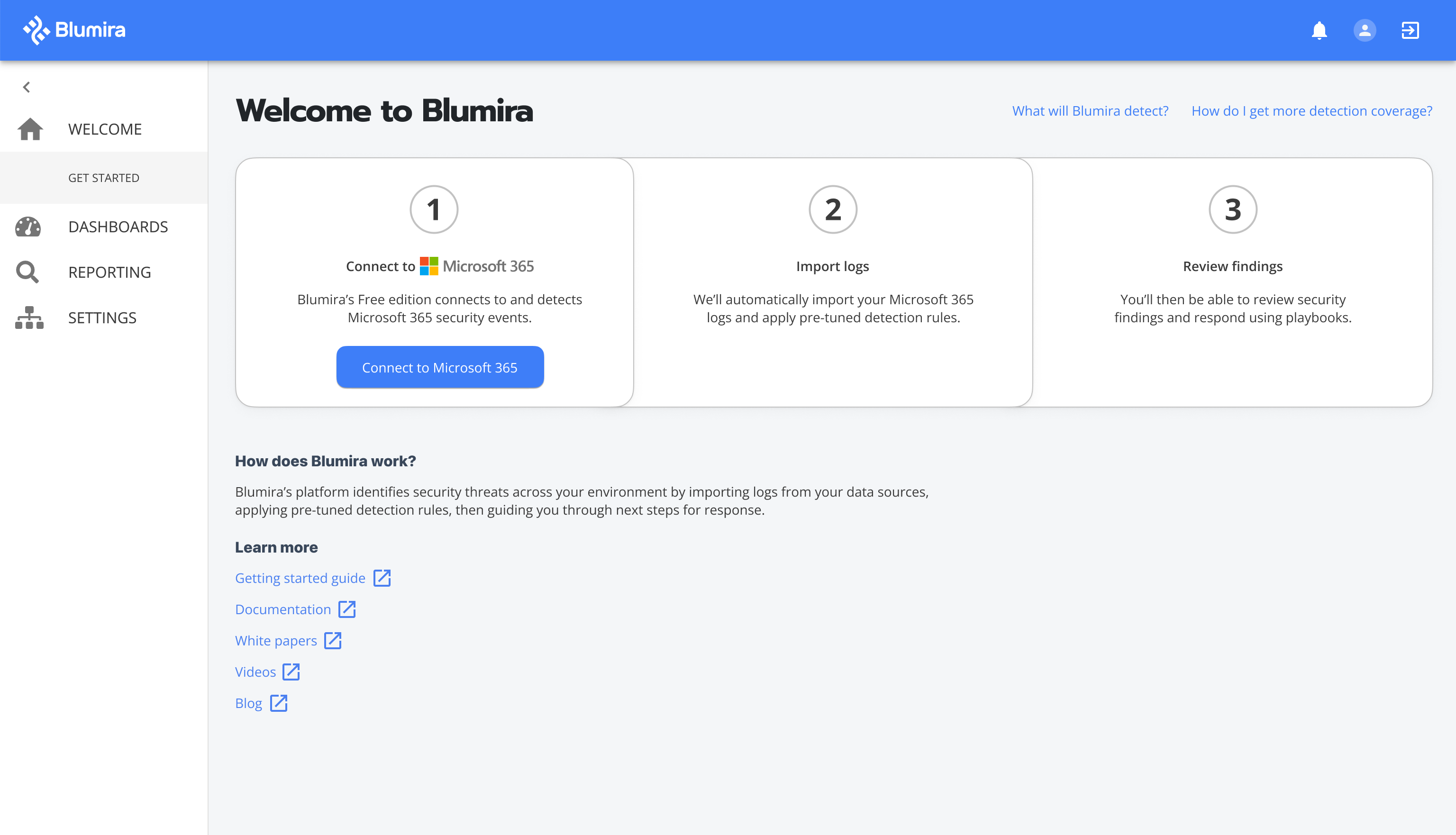 Blumira’s free, self-service cloud security information and event management (SIEM) for Microsoft 365 integrates detection and response. The platform can be deployed in minutes for teams of any size or level of security expertise without additional infrastructure. Once set up, the platform helps protect existing investments by collecting and streaming logs from a number of systems into Blumira’s centralized platform. The platform parses different data and log types’ and helps information technology (IT) teams gain security monitoring for Microsoft 365 with unlimited users and data, as well as access detection and response playbooks with every finding that walks teams through remediation steps, basic reporting and ongoing, automated detection rule updates. Image courtesy of Blumira
Blumira’s free, self-service cloud security information and event management (SIEM) for Microsoft 365 integrates detection and response. The platform can be deployed in minutes for teams of any size or level of security expertise without additional infrastructure. Once set up, the platform helps protect existing investments by collecting and streaming logs from a number of systems into Blumira’s centralized platform. The platform parses different data and log types’ and helps information technology (IT) teams gain security monitoring for Microsoft 365 with unlimited users and data, as well as access detection and response playbooks with every finding that walks teams through remediation steps, basic reporting and ongoing, automated detection rule updates. Image courtesy of Blumira
Find out more at www.blumira.com
Bolster
Automates Digital Risk Protection
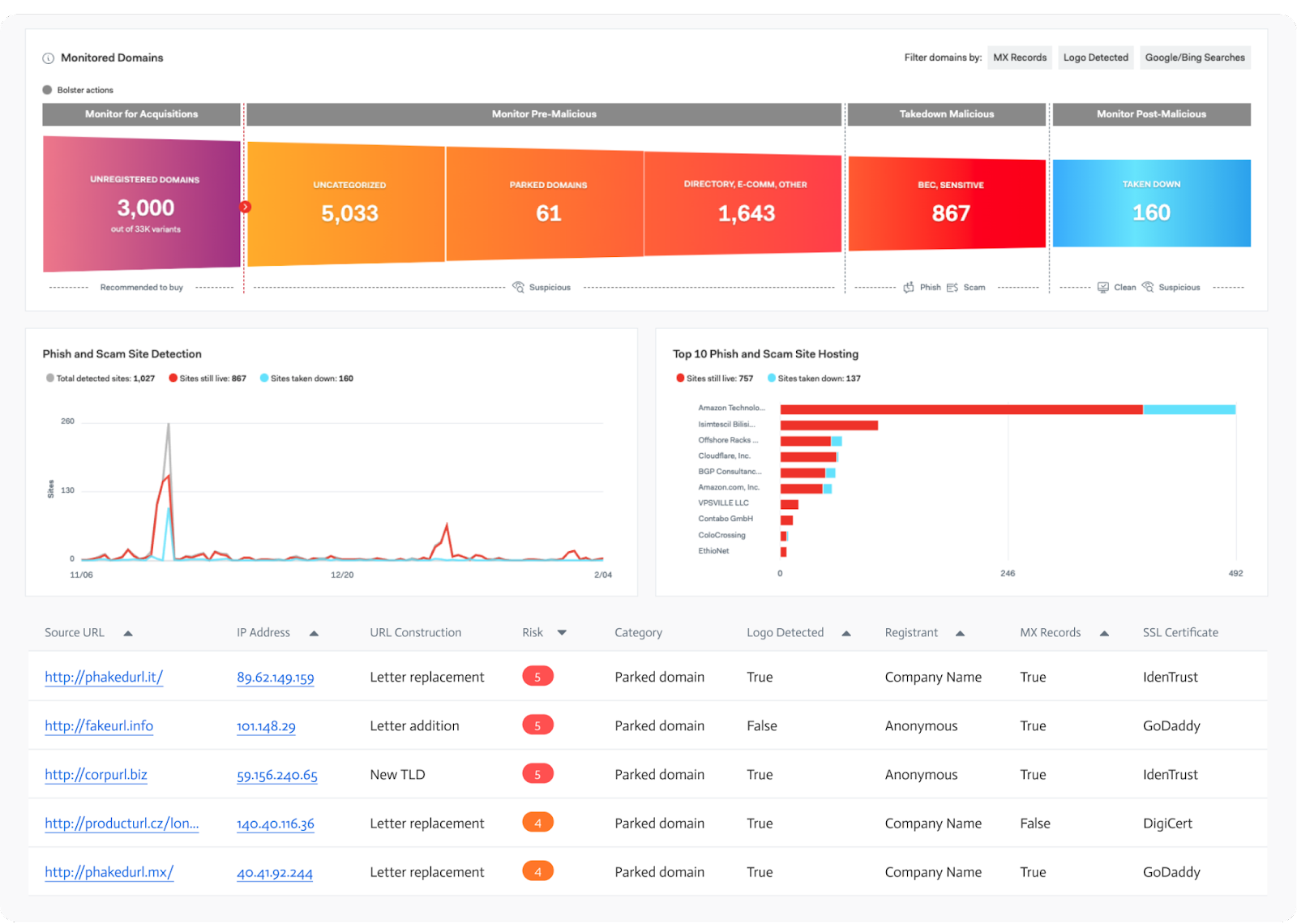 Bolster released three new modules on its digital risk protection platform: social media, app store and dark web monitoring. The platform uses artificial intelligence (AI) to power its domain protection product, which offers detection, analysis and takedown capabilities. The platform’s latest features include detecting and removing social media posts promoting counterfeit products, fake profiles and scam offers; monitoring, detection and takedown of fraudulent apps and scam sites across all major app stores and third-party app stores; and automated detection and intelligence to identify and defend against future attacks that originate in the dark web. Image courtesy of Bolster
Bolster released three new modules on its digital risk protection platform: social media, app store and dark web monitoring. The platform uses artificial intelligence (AI) to power its domain protection product, which offers detection, analysis and takedown capabilities. The platform’s latest features include detecting and removing social media posts promoting counterfeit products, fake profiles and scam offers; monitoring, detection and takedown of fraudulent apps and scam sites across all major app stores and third-party app stores; and automated detection and intelligence to identify and defend against future attacks that originate in the dark web. Image courtesy of Bolster
Find out more at www.bolster.ai
Coalfire
Enhances Compliance and Risk Management
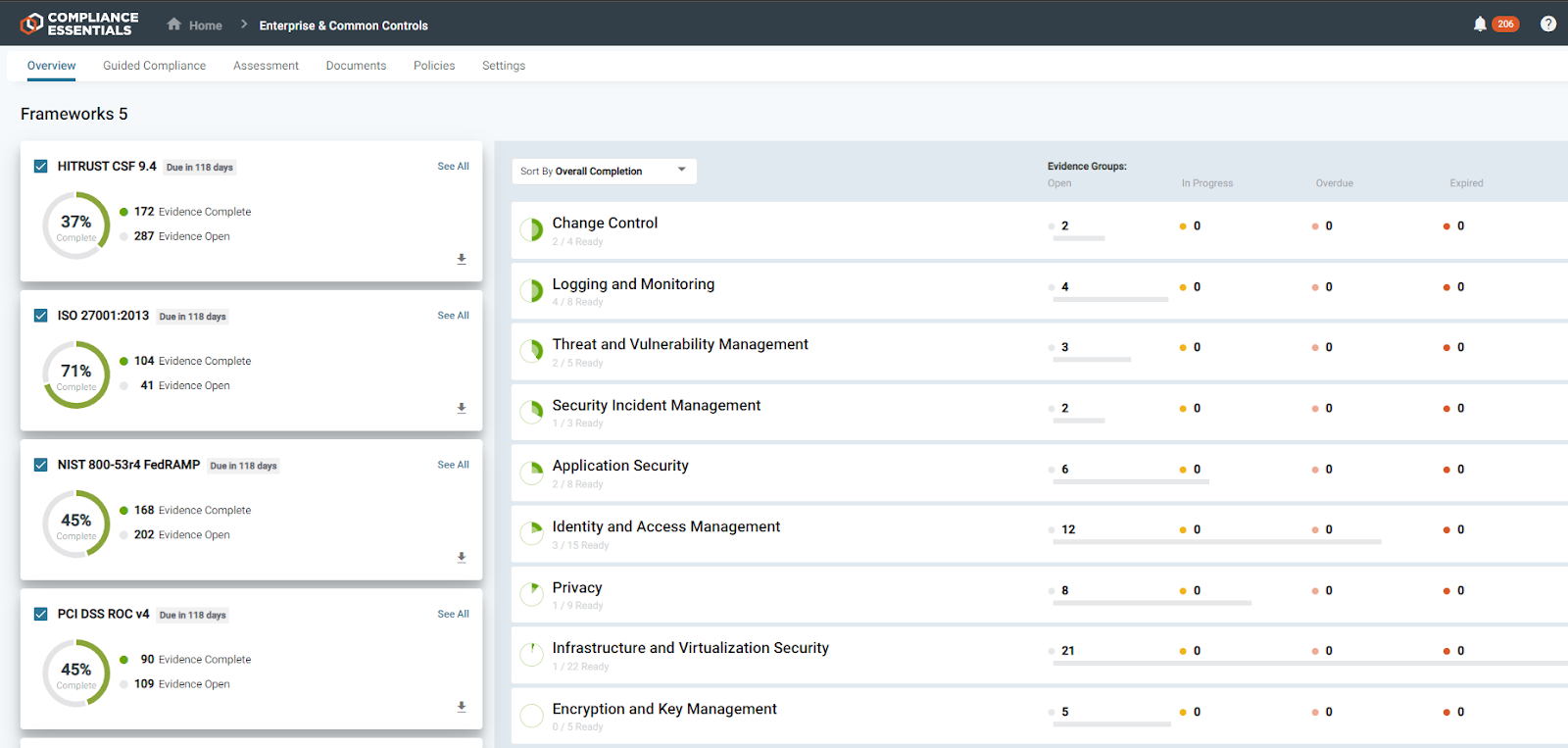 Coalfire Compliance Essentials is an enterprise-grade assessment solution that combines Software as a Service (SaaS) technology with expert guidance to streamline an organization’s compliance management. The solution helps to support frameworks of other compliance automation tools and uses evidence mapping across frameworks to eliminate duplicate activities, allowing organizations to transfer evidence to auditors. The solution helps to enhance workflows, policy management, program visibility, assessments and risk management. It streamlines audit cycles and provides dashboards and reporting for stakeholders responsible for enterprise compliance and risk management. Image courtesy of Coalfire
Coalfire Compliance Essentials is an enterprise-grade assessment solution that combines Software as a Service (SaaS) technology with expert guidance to streamline an organization’s compliance management. The solution helps to support frameworks of other compliance automation tools and uses evidence mapping across frameworks to eliminate duplicate activities, allowing organizations to transfer evidence to auditors. The solution helps to enhance workflows, policy management, program visibility, assessments and risk management. It streamlines audit cycles and provides dashboards and reporting for stakeholders responsible for enterprise compliance and risk management. Image courtesy of Coalfire
Find out more at www.coalfire.com
ColorTokens
Uncovers Cloud Security Risks
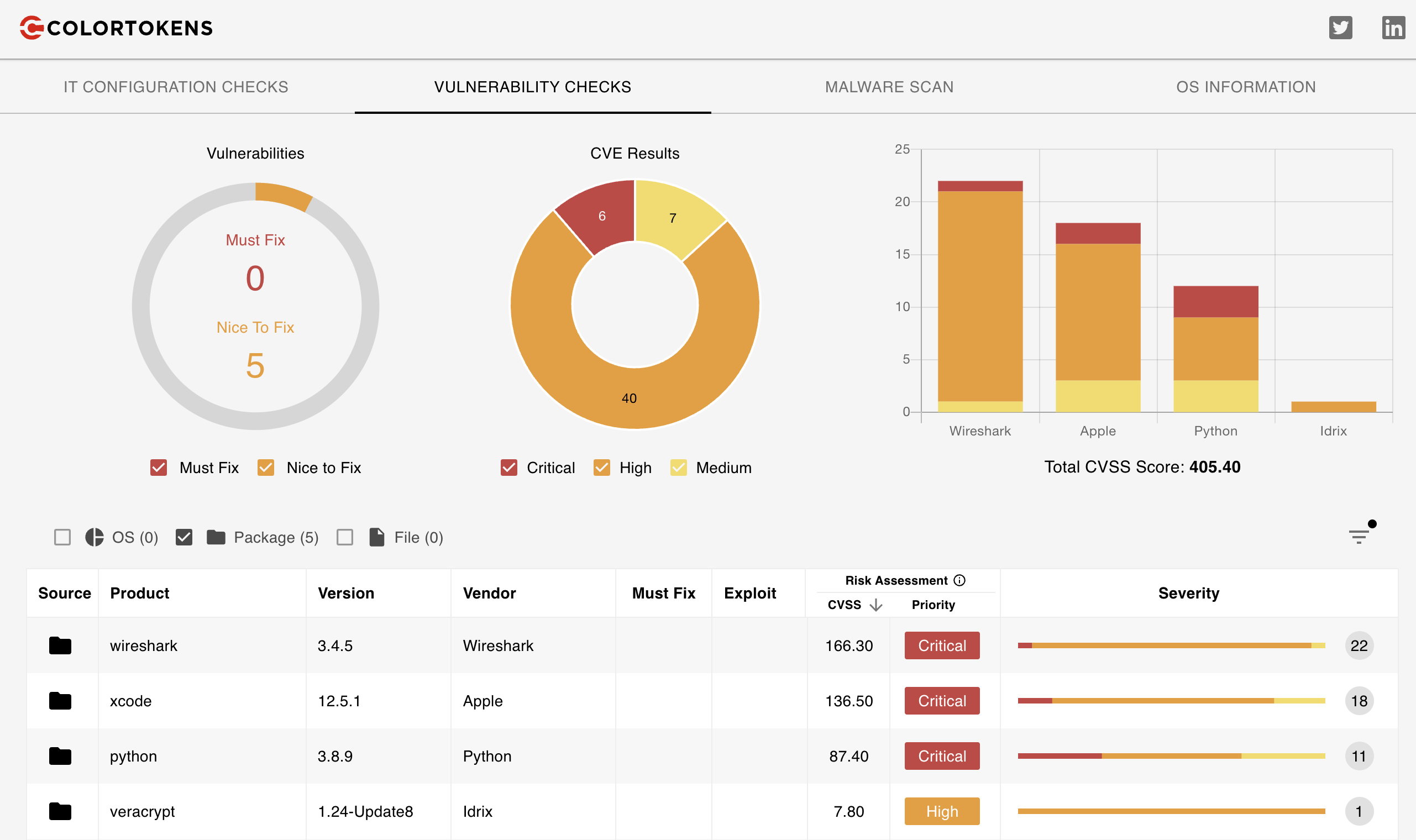 ColorTokens Xcloud can help to find the threats across cloud and container environments. Xcloud combines vulnerability management, malware detection and compliance monitoring in one platform. Xcloud’s ChainScan features help organizations uncover vulnerabilities in critical application libraries and scan container and cloud workloads for software dependencies. This allows enterprises to identify the risks introduced in third-party packages throughout their application software supply chain. Xcloud tracks vulnerabilities and malware from threat intelligence and vulnerability sources. Image courtesy of ColorTokens
ColorTokens Xcloud can help to find the threats across cloud and container environments. Xcloud combines vulnerability management, malware detection and compliance monitoring in one platform. Xcloud’s ChainScan features help organizations uncover vulnerabilities in critical application libraries and scan container and cloud workloads for software dependencies. This allows enterprises to identify the risks introduced in third-party packages throughout their application software supply chain. Xcloud tracks vulnerabilities and malware from threat intelligence and vulnerability sources. Image courtesy of ColorTokens
Find out more at www.colortokens.com
Computer Services Inc.
Detect and Remediate Cyber Threats
 Computer Services Inc.’s (CSI) Security and Information and Event Management as a Service (SIEMaaS) solution helps organizations to mitigate cybersecurity risk. SIEMaaS enables organizations to avoid the challenges associated with handling cybersecurity internally, including hiring staff with the right expertise, purchasing software solutions or configuring solutions to send alerts. As a component of a layered cybersecurity approach, this solution provides analysis of attacks in an environment by collecting and reviewing logs for connected devices across a technology environment, detecting anomalies, delivering incident response and remediation, and minimizing false positives. Image courtesy of CSI
Computer Services Inc.’s (CSI) Security and Information and Event Management as a Service (SIEMaaS) solution helps organizations to mitigate cybersecurity risk. SIEMaaS enables organizations to avoid the challenges associated with handling cybersecurity internally, including hiring staff with the right expertise, purchasing software solutions or configuring solutions to send alerts. As a component of a layered cybersecurity approach, this solution provides analysis of attacks in an environment by collecting and reviewing logs for connected devices across a technology environment, detecting anomalies, delivering incident response and remediation, and minimizing false positives. Image courtesy of CSI
Find out more at www.csiweb.com
Delinea
Provides Privileged Access Management
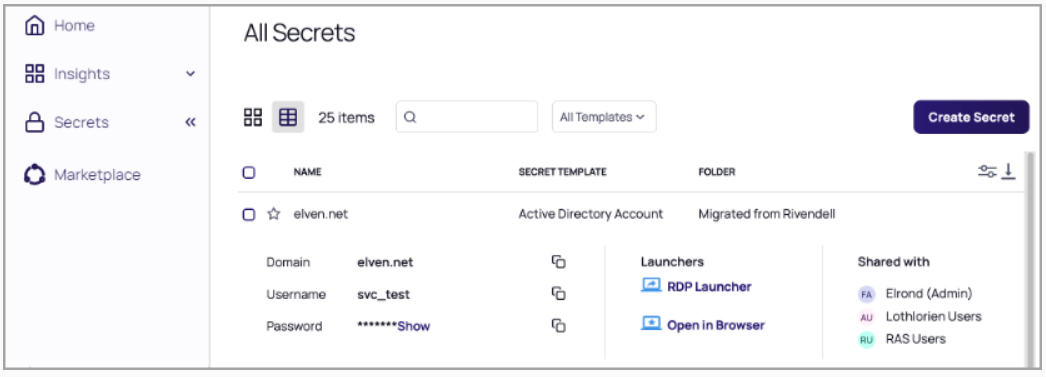 Delinea integrated its Remote Access Service offering with Secret Server. The capability provides a virtual private network (VPN)-less, browser-based remote desktop protocol (RDP)/SSH, also known as Secure Shell or Secure Socket Shell, session management for contractors and remote employees. Remote Access Service requires no end-user client or VPN connection to support theenvironments and systems used by an extended workforce. The latest release includes enhancements to password complexity rules, revisions to incident response practices, anduser-interface improvements. Remote Access Service works with Secret Server on-premises and in the cloud. Image courtesy of Delinea
Delinea integrated its Remote Access Service offering with Secret Server. The capability provides a virtual private network (VPN)-less, browser-based remote desktop protocol (RDP)/SSH, also known as Secure Shell or Secure Socket Shell, session management for contractors and remote employees. Remote Access Service requires no end-user client or VPN connection to support theenvironments and systems used by an extended workforce. The latest release includes enhancements to password complexity rules, revisions to incident response practices, anduser-interface improvements. Remote Access Service works with Secret Server on-premises and in the cloud. Image courtesy of Delinea
Find out more at www.delinea.com
Dig Security
Enables Data Loss Prevention With Detection & Response
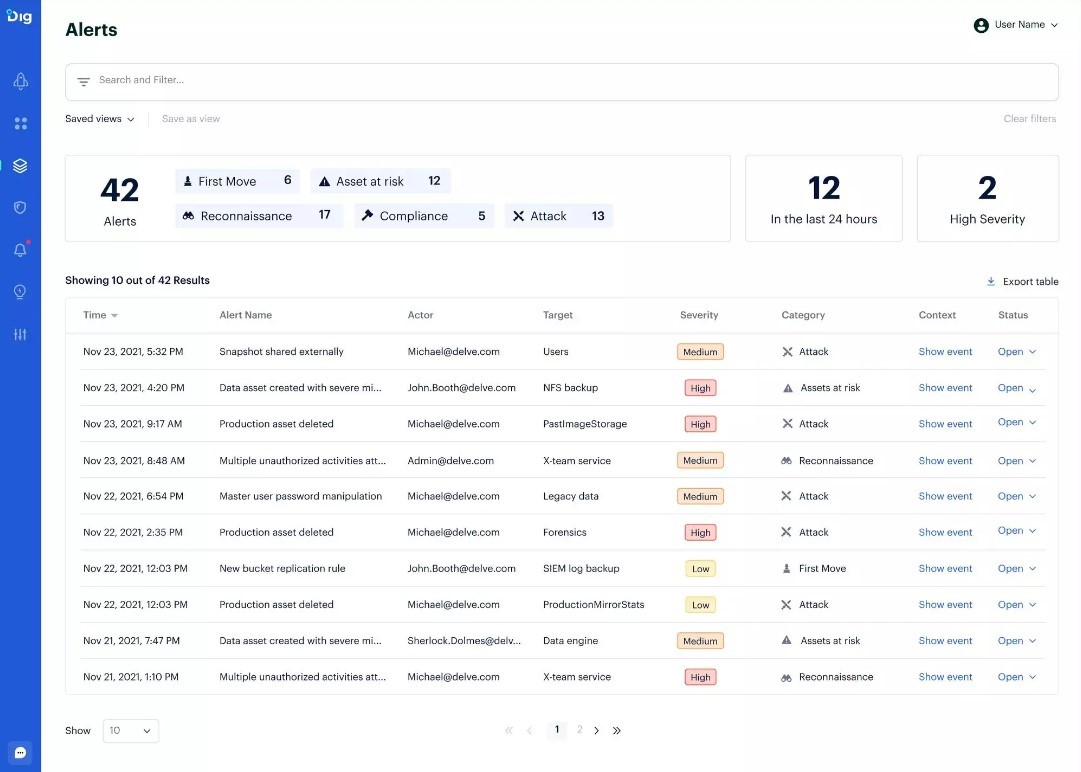
Dig Security‘s Dig Data Security Platform enables organizations to discover, classify and govern their cloud data. With organizations shifting to complex environments with dozens of database types across clouds, monitoring and detecting data exfiltration and policy violations have become a complex problem with limited fragmented solutions. The platform combines data security posture management, data loss prevention (DLP), and data detection and response capabilities into a platform to provide detection and response. It supports all cloud infrastructures, including Amazon Web Services (AWS), Azure, Google Cloud Platform (GCP), and data clouds like Snowflake and Databricks. Image courtesy of Dig Data
Find out more at www.dig.security
DoControl
Helps Apply Data Access Security Controls
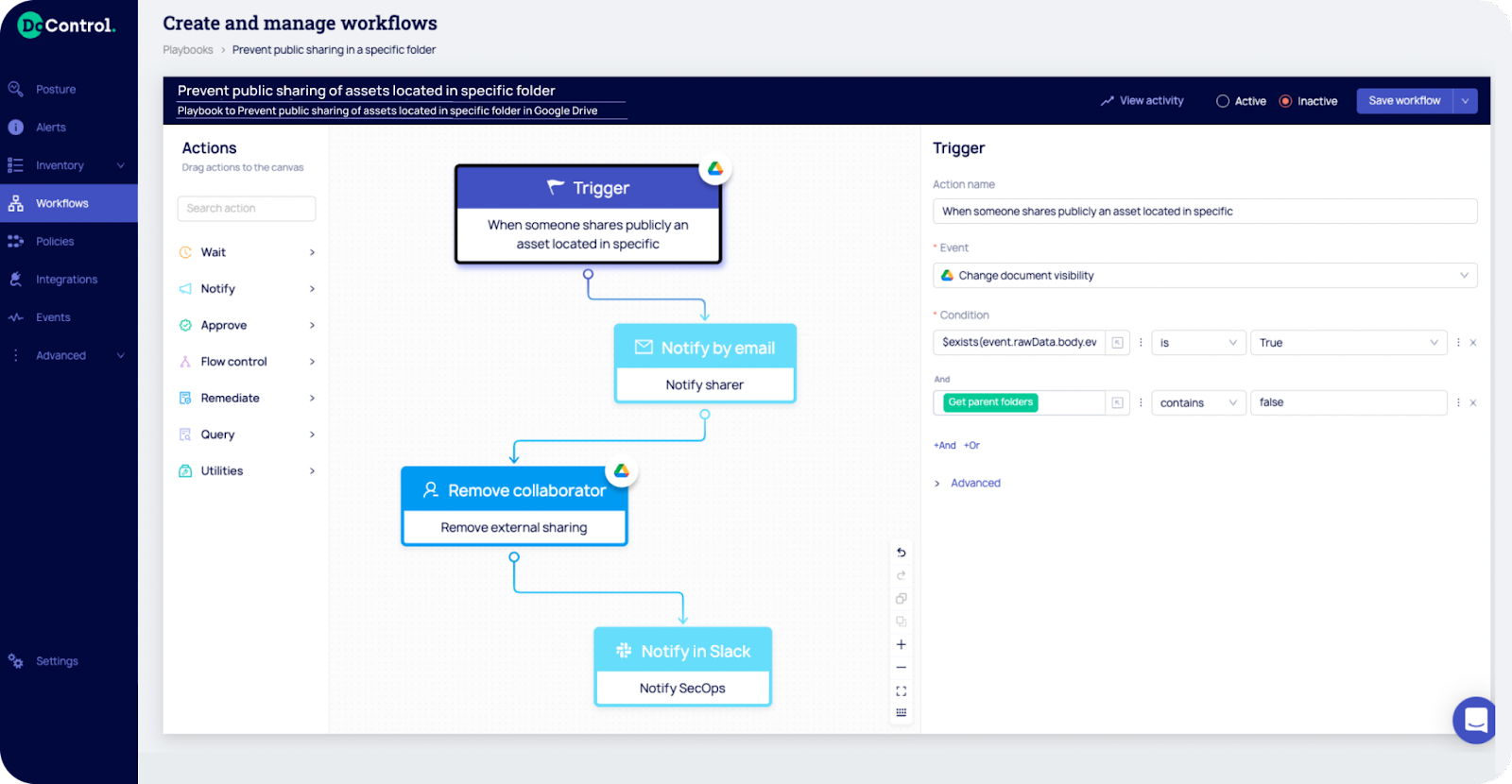
DoControl’s No-Code SaaS Security Workflows Platform helps to extend zero trust beyond the identity, device and network into the SaaS data layer. The platform’s security workflows allow IT and security teams to enforce SaaS security policies throughout disparate applications being used by organizations. By overcoming the problem associated with applying effective data access security controls to critical SaaS applications, IT and security teams can now address a wide range of use cases driven by over 500 SaaS event types and select the actions, triggers, remediation steps and paths taken. Image courtesy of DoControl
Find out more at www.docontrol.io
ExtraHop
Extends Detection
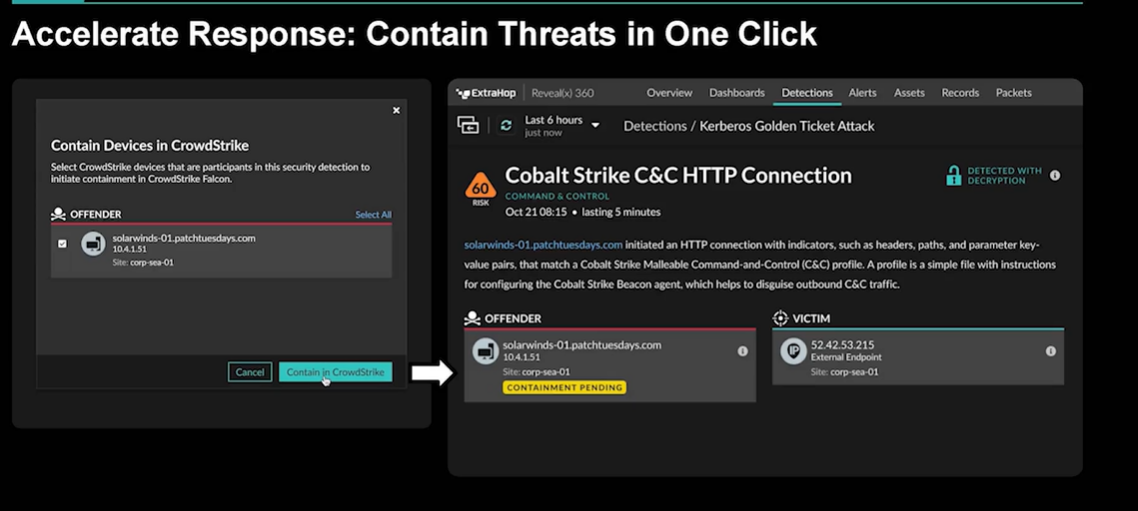 ExtraHop’s Reveal(x) response integration with Crowdstrike helps to expand extended detection and response (XDR), enabling users to quarantine individual assets from a detection directly within Reveal(x) and then pivot into an investigation workflow. Reveal(x) 360 correlates indicators of compromise (IOCs) from CrowdStrike Falcon X and security telemetry from the CrowdStrike Falcon platform with network details and behavioral insights. The data is correlated and contextualized in the Reveal(x) console. Security teams can detect threats observed on the network, such as network privilege escalation, lateral movement, suspicious remote access connections and data exfiltration. They also can thwart attack techniques occurring on the endpoint, including ransomware, local file enumeration, process spawning, and code execution. Image courtesy of ExtraHop and Crowdstrike
ExtraHop’s Reveal(x) response integration with Crowdstrike helps to expand extended detection and response (XDR), enabling users to quarantine individual assets from a detection directly within Reveal(x) and then pivot into an investigation workflow. Reveal(x) 360 correlates indicators of compromise (IOCs) from CrowdStrike Falcon X and security telemetry from the CrowdStrike Falcon platform with network details and behavioral insights. The data is correlated and contextualized in the Reveal(x) console. Security teams can detect threats observed on the network, such as network privilege escalation, lateral movement, suspicious remote access connections and data exfiltration. They also can thwart attack techniques occurring on the endpoint, including ransomware, local file enumeration, process spawning, and code execution. Image courtesy of ExtraHop and Crowdstrike
Find out more at www.extrahop.com
Keeper
Enables Zero Trust Security
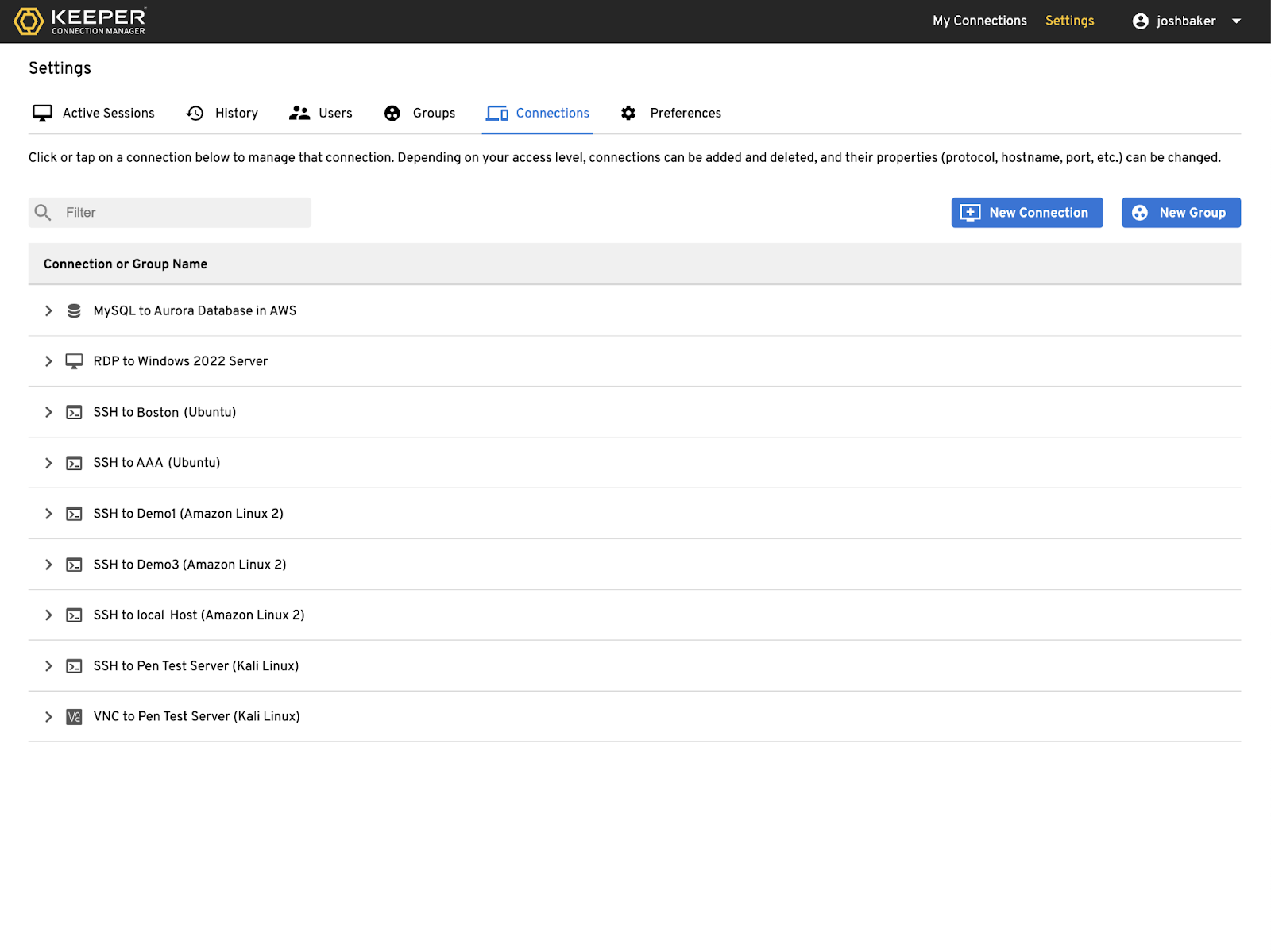 The Keeper Connection Manager (KCM) is a remote-access gateway that provides DevOps and IT teams with secure access to RDP, SSH, virtual network computing, MySQL and Kubernetes endpoints through any standard web browser. The approach helps organizations enable zero-trust security, with features such as least-privilege access, role-based access control and multi-factor authentication. The product supports several use cases, including remote infrastructure access for IT teams connecting to databases, SSH and Kubernetes nodes; privileged access management with session recording and auditability; VPN replacement with zero trust access to systems following least-privilege principles; and RDP for distributed workforces. Image courtesy of Keeper
The Keeper Connection Manager (KCM) is a remote-access gateway that provides DevOps and IT teams with secure access to RDP, SSH, virtual network computing, MySQL and Kubernetes endpoints through any standard web browser. The approach helps organizations enable zero-trust security, with features such as least-privilege access, role-based access control and multi-factor authentication. The product supports several use cases, including remote infrastructure access for IT teams connecting to databases, SSH and Kubernetes nodes; privileged access management with session recording and auditability; VPN replacement with zero trust access to systems following least-privilege principles; and RDP for distributed workforces. Image courtesy of Keeper
Find out more at www.keepersecurity.com
Lookout
Manages and Classifies Sensitive Data
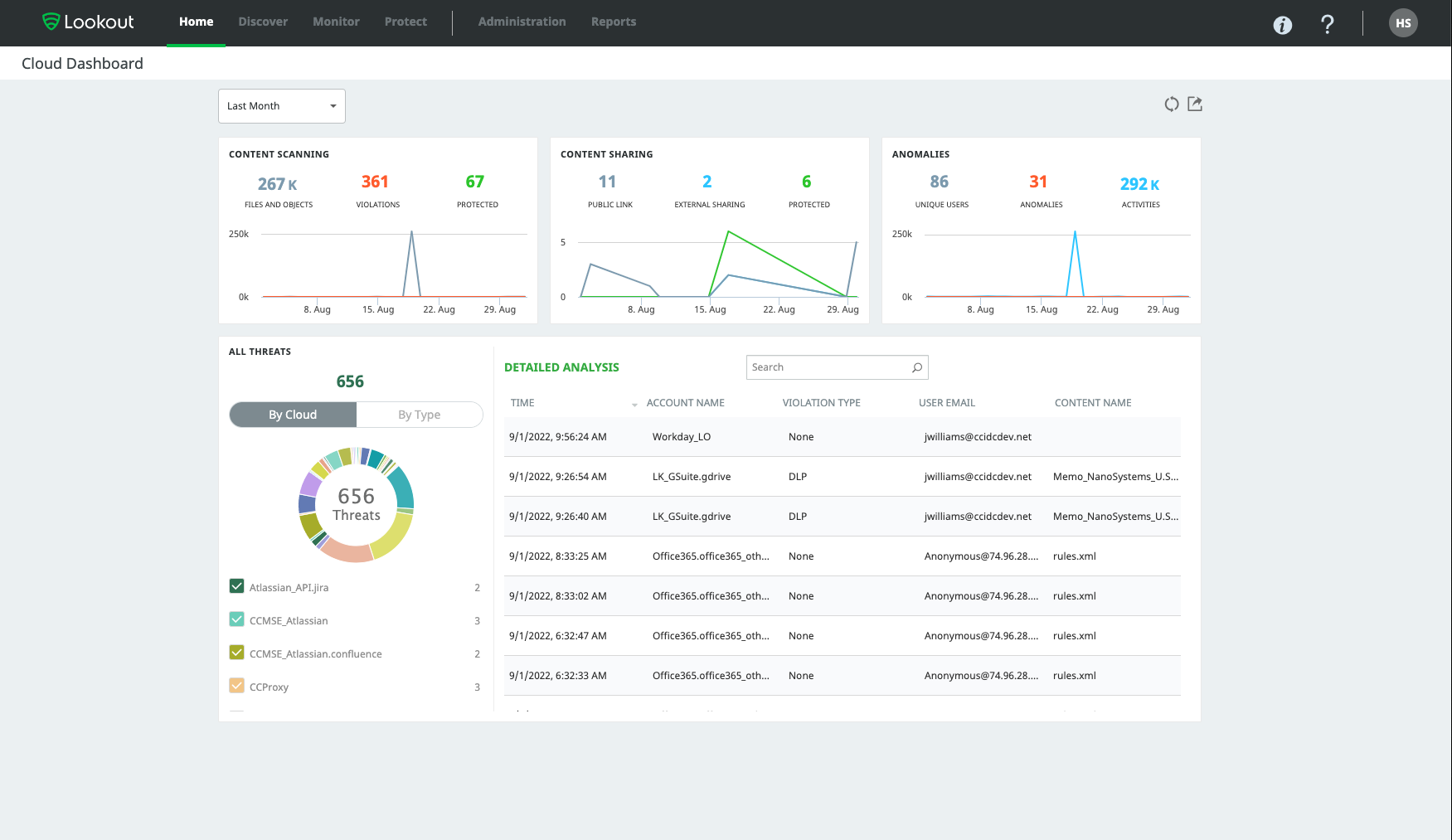
The Lookout Cloud Security Platform — a Security Service Edge (SSE) solution — combines cloud access security broker (CASB), zero trust network access (ZTNA) and secure web gateway (SWG). The platform detects malicious content and classifies sensitive data while monitoring the risk level of endpoints on the network. The solution combines data security, access control, threat protection, security monitoring and acceptable use control functionality, allowing organizations to modify access and protect data using DLP capabilities to encrypt and restrict data sharing so only authorized users have access. It also delivers automated assessments of all cloud apps and infrastructure to ensure proper configuration. Image courtesy of Lookout
Find out more at www.lookout.com
Netenrich
Keeps Cybersecurity Operations Aligned to Risk
 The Netenrich Resolution Intelligence Cloud helps chief information security officers (CISOs) and security teams mitigate cybersecurity threats. Resolution Intelligence Cloud is a data analytics SaaS platform for managing security and digital operations. It helps CISOs transform security and digital operations by ingesting security and operations data, identifying pre-incident situations, ranking them by business risk, and correlating context for proactive resolution. It also operationalizes Google Chronicle to deliver insights that speed resolution and keep operations aligned to risk. The platform applies analytics and machine learning (ML) across operations and security data, including data from hybrid cloud environments. Image courtesy of Netenrich
The Netenrich Resolution Intelligence Cloud helps chief information security officers (CISOs) and security teams mitigate cybersecurity threats. Resolution Intelligence Cloud is a data analytics SaaS platform for managing security and digital operations. It helps CISOs transform security and digital operations by ingesting security and operations data, identifying pre-incident situations, ranking them by business risk, and correlating context for proactive resolution. It also operationalizes Google Chronicle to deliver insights that speed resolution and keep operations aligned to risk. The platform applies analytics and machine learning (ML) across operations and security data, including data from hybrid cloud environments. Image courtesy of Netenrich
Find out more at www.netenrich.com
SlashNext
Protects Users Against Mobile Phishing
SlashNext’s Mobile Security Personal and Home editions help protect mobile device owners against the growing threat of phishing attempts on SMS/text, links and apps, while offering privacy for users’ data. The solution adds layers of security to users’ personal devices and allows businesses to protect company data and maintain employees’ privacy. The solution blocks link-based SMS phishing attacks, the first attack stage in business text compromise (BTC). SlashNext Mobile Security Personal and Home editions are available on Apple and Android app stores. Image courtesy of SlashNext
Find out more at www.slashnext.com
SPHERE
Reduces Internal Threat Exposures
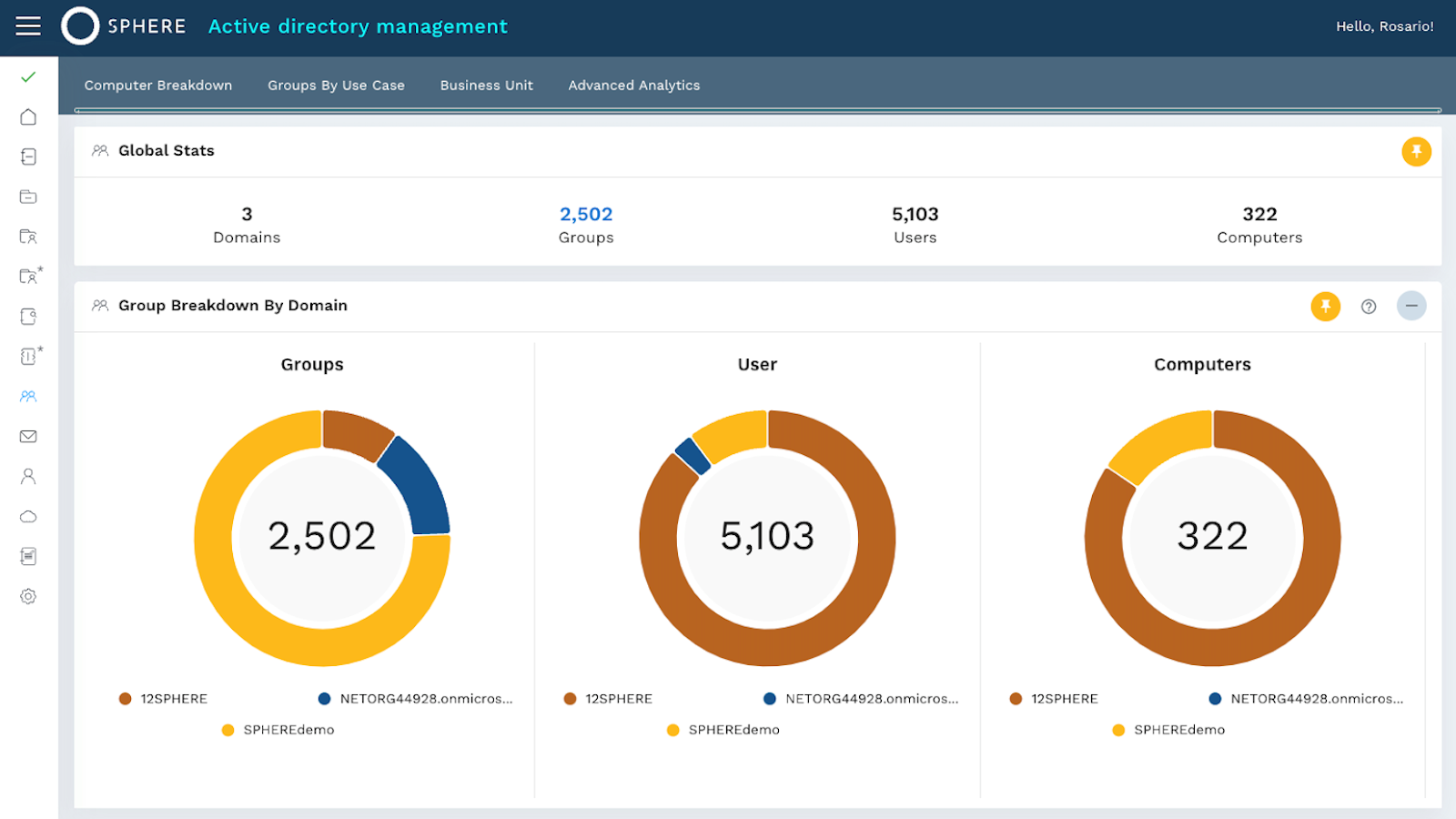 SPHERE’s SPHEREboard 6.2 introduces automatic remediation and visibility into an organization’s security risks and privileged access. Version 6.2 introduces Stock and Flow Reporting to help organizations reduce their internal threat posture. This tool allows users to oversee remediation progress, pinpoint process breaks that introduce risks into their environment, and understand the security improvements they are making over time. Image courtesy of SPHERE
SPHERE’s SPHEREboard 6.2 introduces automatic remediation and visibility into an organization’s security risks and privileged access. Version 6.2 introduces Stock and Flow Reporting to help organizations reduce their internal threat posture. This tool allows users to oversee remediation progress, pinpoint process breaks that introduce risks into their environment, and understand the security improvements they are making over time. Image courtesy of SPHERE
Find out more at www.sphereco.com
StackHawk
Scans APIs for Cyber Vulnerabilities
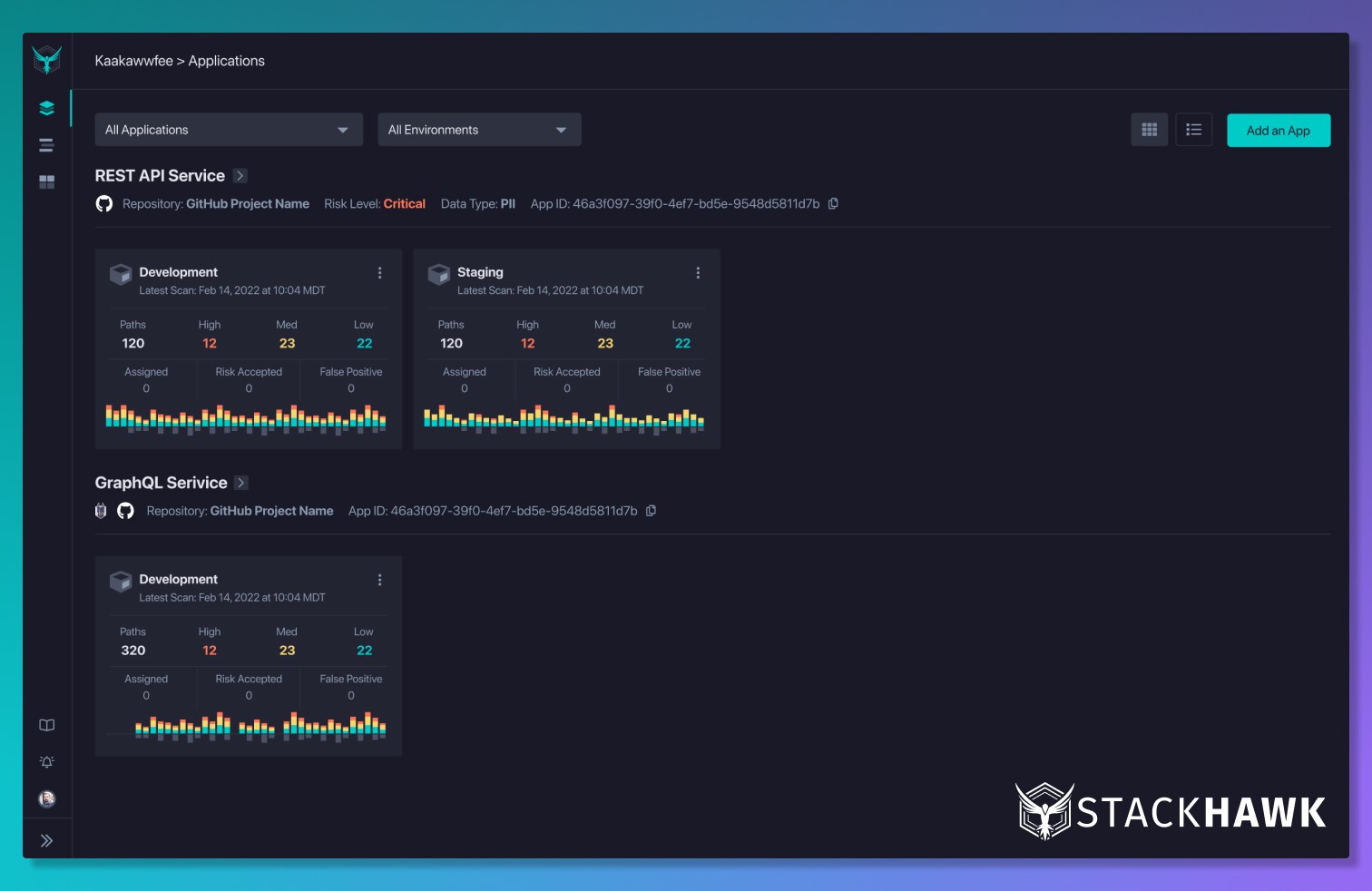 StackHawk’s Deeper API Security Test Coverage helps developers scan the entire API layer to uncover potential vulnerabilities. With this release, developers have the ability to test APIs. The solution makes application security testing part of software delivery so that engineers can find and fix application security bugs at every stage of the software development lifecycle. The solution allows teams to leverage existing automated testing tools to guide discovery of the paths and endpoints, provide custom test data to be used during scans and cover proprietary use cases for security testing. Image courtesy of StackHawk
StackHawk’s Deeper API Security Test Coverage helps developers scan the entire API layer to uncover potential vulnerabilities. With this release, developers have the ability to test APIs. The solution makes application security testing part of software delivery so that engineers can find and fix application security bugs at every stage of the software development lifecycle. The solution allows teams to leverage existing automated testing tools to guide discovery of the paths and endpoints, provide custom test data to be used during scans and cover proprietary use cases for security testing. Image courtesy of StackHawk
Find out more at www.stackhawk.com
ThreatModeler
Helps Detect & Remediate Security Flaws
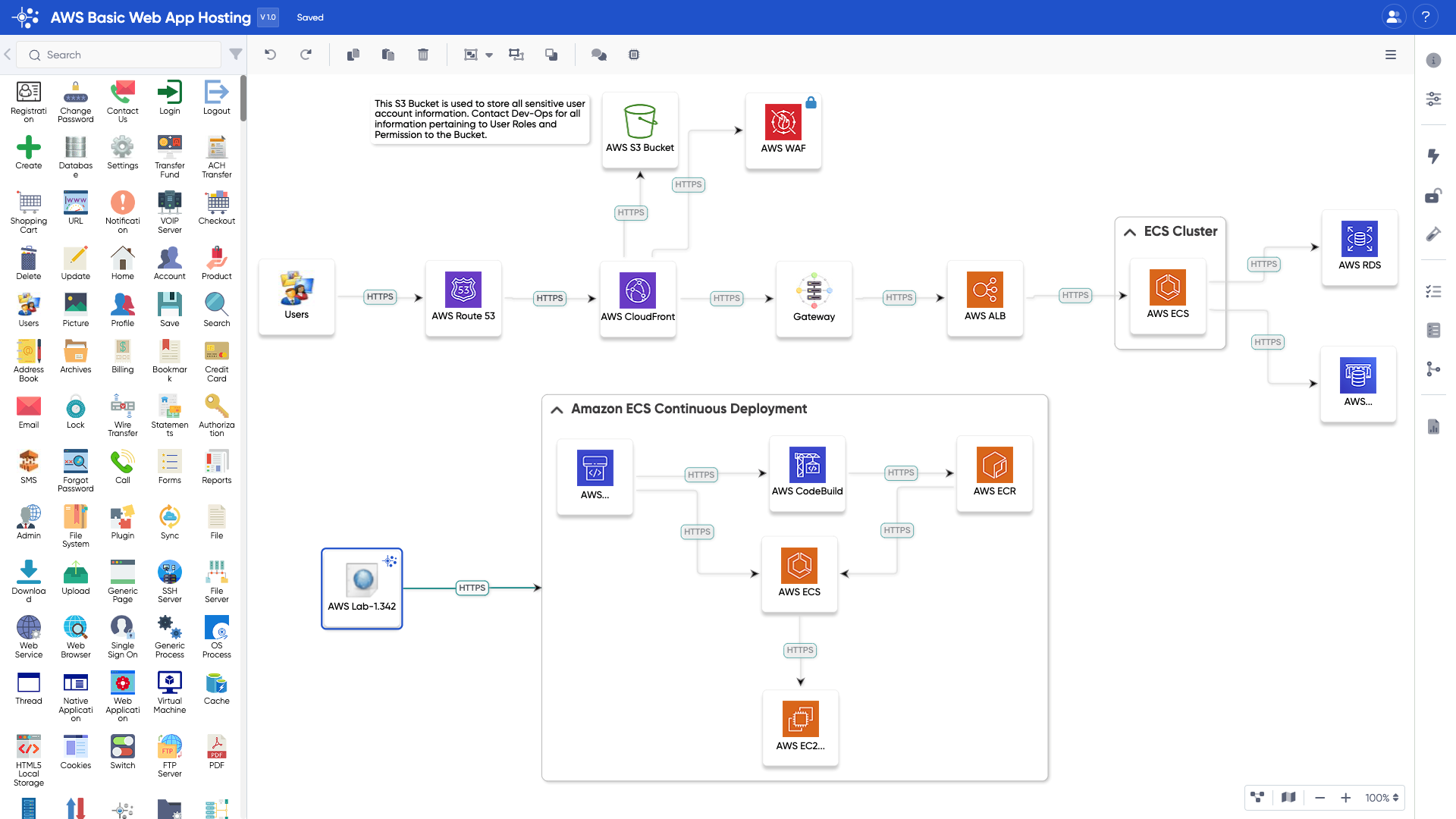 ThreatModeler 6.0 provides end users with information, tools and collaboration options to facilitate the management of threat models for large enterprises. Without relying on code, the platform provides a common language to enable developers and security teams to communicate and shift security left of the cloud development lifecycle. The 6.0 update enhances approvals workflows with the ability to tag collaborators and assign tasks with in-platform notifications and enhancements to audit, development and compliance reporting. Users can specify the time period, activity and components of each report to enable a view of threats across the security environment. The custom reporting tool enables teams to compile both simplistic and complex information for review and remediation. Image courtesy of ThreatModeler
ThreatModeler 6.0 provides end users with information, tools and collaboration options to facilitate the management of threat models for large enterprises. Without relying on code, the platform provides a common language to enable developers and security teams to communicate and shift security left of the cloud development lifecycle. The 6.0 update enhances approvals workflows with the ability to tag collaborators and assign tasks with in-platform notifications and enhancements to audit, development and compliance reporting. Users can specify the time period, activity and components of each report to enable a view of threats across the security environment. The custom reporting tool enables teams to compile both simplistic and complex information for review and remediation. Image courtesy of ThreatModeler
Find out more at www.threatmodeler.com
Tigera
Mitigates Risk and Cyberattacks
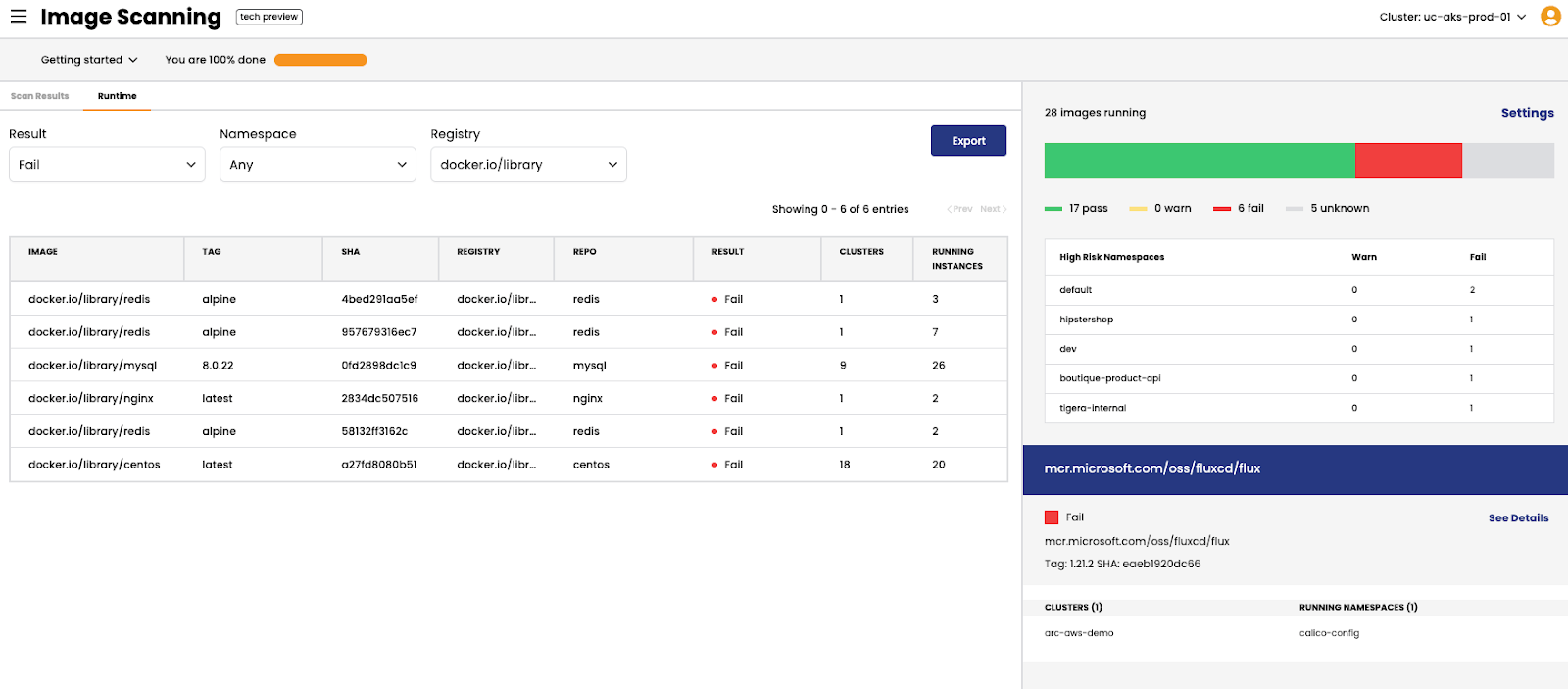 The Tigera cloud-native application protection platform (CNAPP), Calico Cloud, applies zero trust to reduce the application’s attack surface. The platform uses machine learning to combat runtime security risks from known and zero-day threats to enable compliance and prioritize risk mitigation and attacks through security policy changes. The container security features on Calico Cloud include image scanning, vulnerability management with blocking failed images, visibility into high-risk workloads running in the environment, and more. By identifying potential vulnerabilities in the build phase of the CI/CD pipeline, users can leverage a shift-left approach to security. Image courtesy of Tigera
The Tigera cloud-native application protection platform (CNAPP), Calico Cloud, applies zero trust to reduce the application’s attack surface. The platform uses machine learning to combat runtime security risks from known and zero-day threats to enable compliance and prioritize risk mitigation and attacks through security policy changes. The container security features on Calico Cloud include image scanning, vulnerability management with blocking failed images, visibility into high-risk workloads running in the environment, and more. By identifying potential vulnerabilities in the build phase of the CI/CD pipeline, users can leverage a shift-left approach to security. Image courtesy of Tigera
Find out more at www.calicocloud.io
Valtix
Secures Multi-Cloud Networks
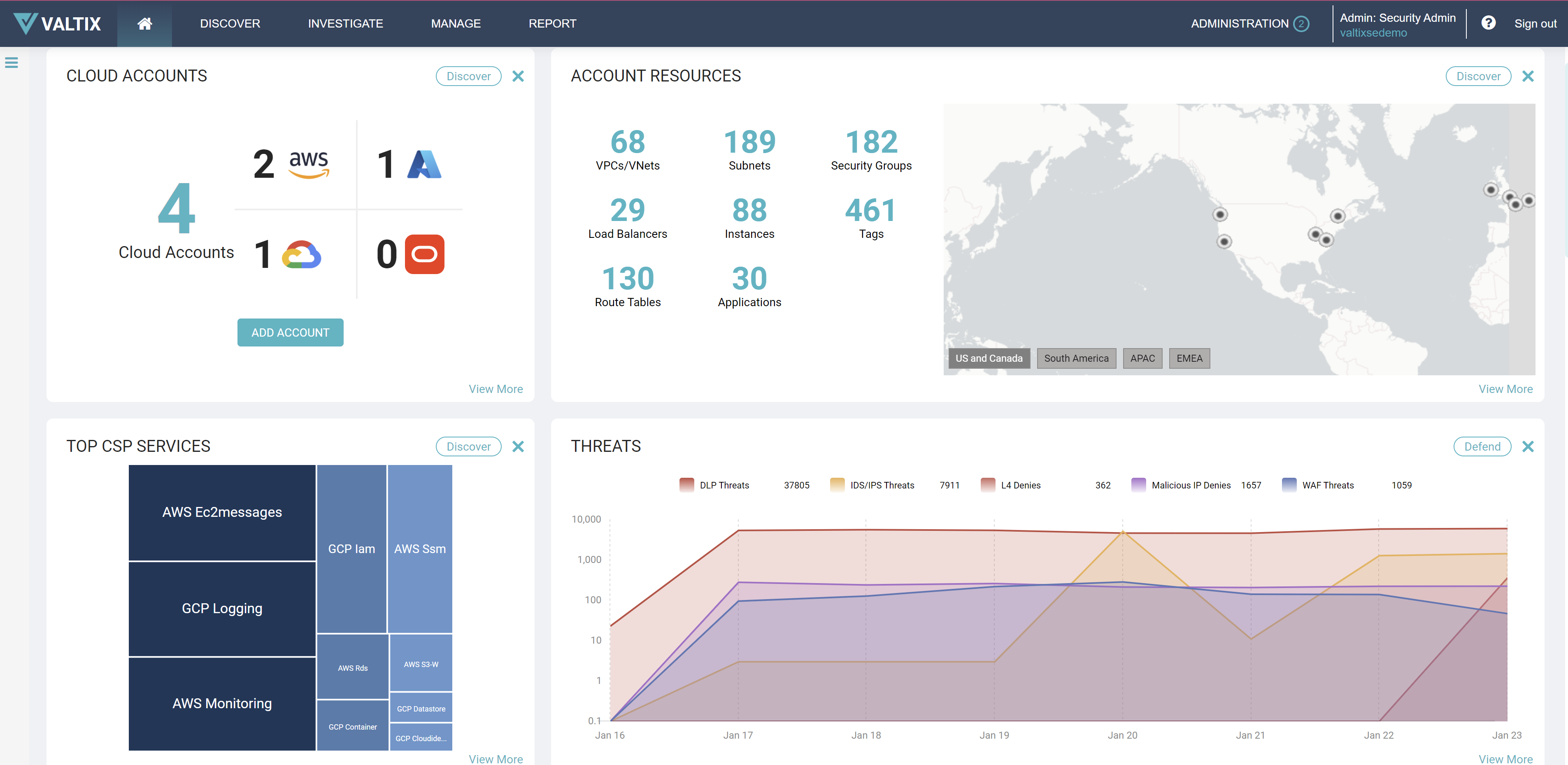 The Valtix Multi-Cloud Security Platform is a multi-cloud network security platform delivered as a service. Powered by a cloud-native architecture, the platform can help enterprises achieve cloud security to stop cloud security threats, such as inbound remote exploits, east-west lateral movement, and outbound data exfiltration, including command and control. With the platform, users can detect new apps and changes that impact network security to automate policy, deploy network security control points across clouds, and have visibility to threats, including malicious domains, geolocation, exploits, and outbound communications. Image courtesy of Valtix
The Valtix Multi-Cloud Security Platform is a multi-cloud network security platform delivered as a service. Powered by a cloud-native architecture, the platform can help enterprises achieve cloud security to stop cloud security threats, such as inbound remote exploits, east-west lateral movement, and outbound data exfiltration, including command and control. With the platform, users can detect new apps and changes that impact network security to automate policy, deploy network security control points across clouds, and have visibility to threats, including malicious domains, geolocation, exploits, and outbound communications. Image courtesy of Valtix
Find out more at www.valtix.com
Viakoo
Helps Manage Enterprise IoT Devices
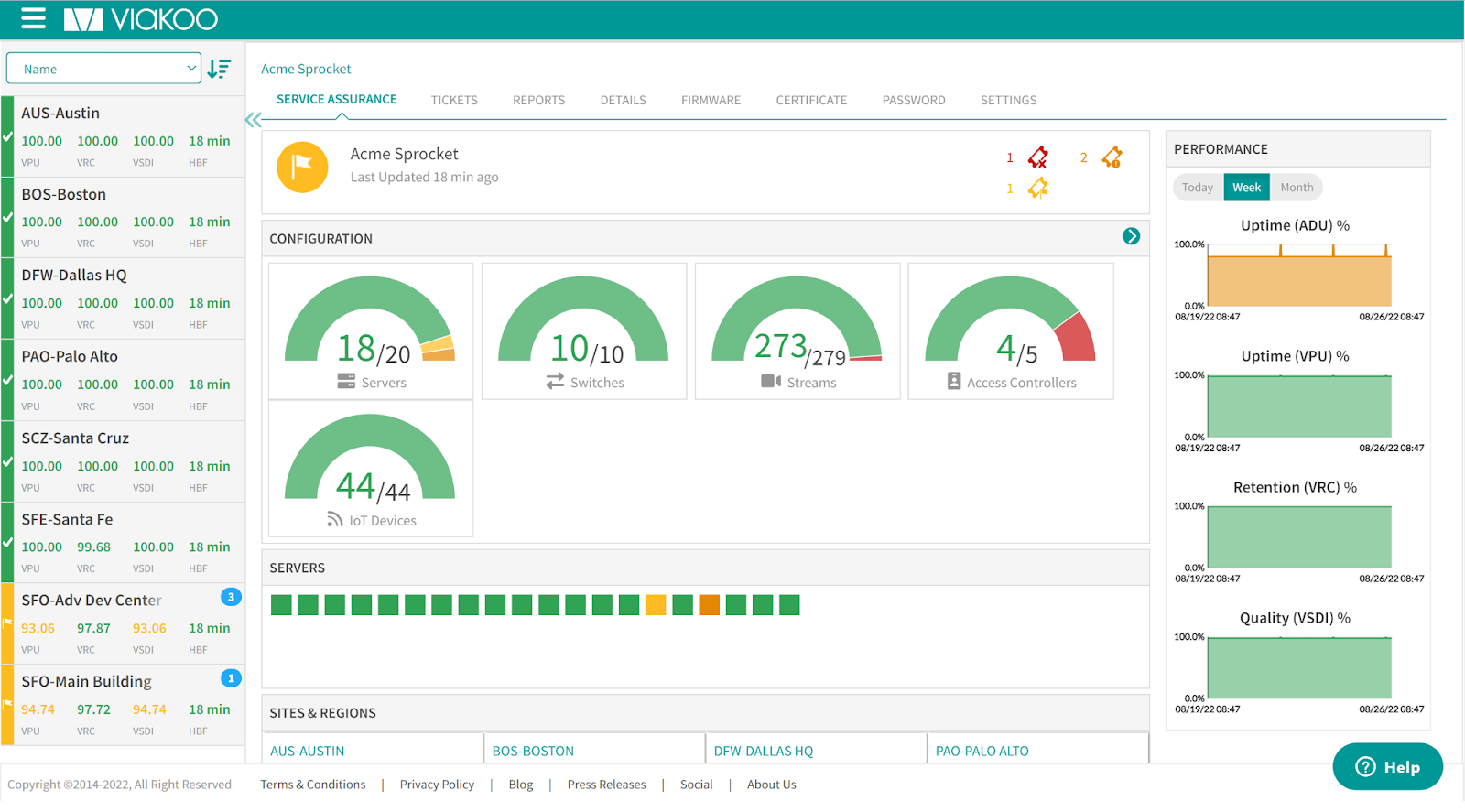 The Viakoo Action Platform helps provide vulnerability scanning, device classification, remediation, and repatriation, which allows organizations to quickly identify and fix security vulnerabilities on Internet of Things (IoT) devices. The IoT device management platform provides a remediation solution, including patching and configuration management and the ability to remotely patch firmware, update certificates and password policy remediation. The platform manages firmware updates, zero trust certificate provisioning and management, and password enforcement. The platform allows organizations to view a number of IoT devices, including medical equipment, point-of-sales systems, HVAC, building access systems, video security and other IP-based devices. Image courtesy of Viakoo
The Viakoo Action Platform helps provide vulnerability scanning, device classification, remediation, and repatriation, which allows organizations to quickly identify and fix security vulnerabilities on Internet of Things (IoT) devices. The IoT device management platform provides a remediation solution, including patching and configuration management and the ability to remotely patch firmware, update certificates and password policy remediation. The platform manages firmware updates, zero trust certificate provisioning and management, and password enforcement. The platform allows organizations to view a number of IoT devices, including medical equipment, point-of-sales systems, HVAC, building access systems, video security and other IP-based devices. Image courtesy of Viakoo
Find out more at www.viakoo.com
Vulcan Cyber
Addresses Cybersecurity Risk Management
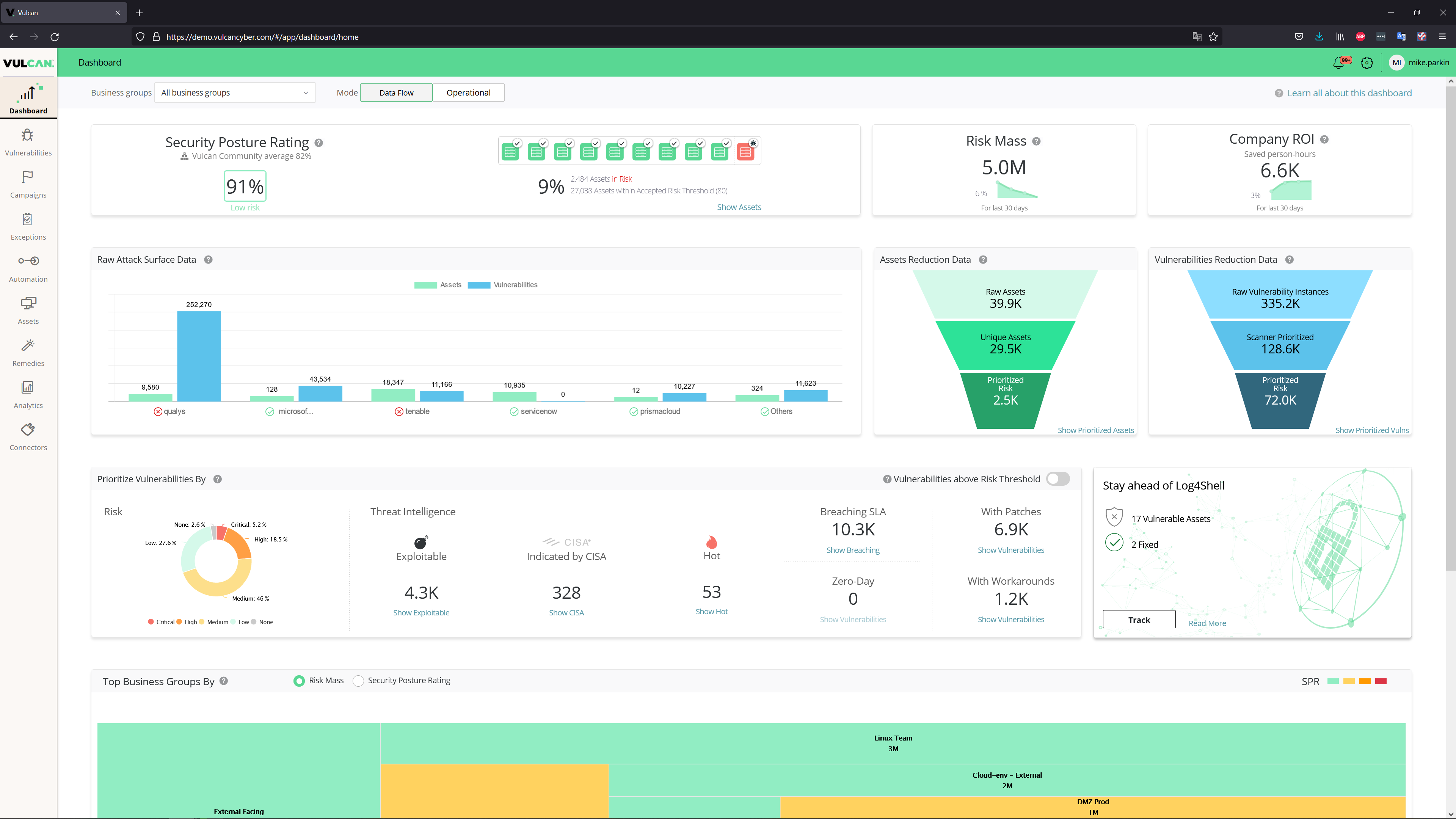
The Vulcan Cyber vulnerability risk management platform collects and aggregates data from cloud, application, infrastructure and endpoint vulnerability sources, prioritizing risks that pose the biggest threat to organizations. The platform’s updates include a security analytics dashboard, a security posture rating that measures cyber risk specific to an organization, and vulnerability risk correlation with vulnerability clusters. Organizations can use the cyber risk management platform to help reduce vulnerability risk through cloud and application vulnerability remediation and connect with the tools IT security teams already use, including vulnerability scan and asset data sources. Image courtesy of Vulcan Cyber
Find out more at www.vulcan.io






