Alcatraz AI
Uses AI for Identity Verification

The Alcatraz AI Rock combines advanced artificial intelligence (AI) and 3D sensing technologies to verify identity. The Rock is compliant with ONVIF standards and can function as an ONVIF camera. The solution is certified with Profile S and Profile T to provide Internet Protocol (IP)-based video streaming. The Rock aims to mitigate tailgating in access control by detecting breaches in real time. The solution can be configured to send an alert to the access control system when an unauthorized user follows an authenticated user through a door. Alcatraz AI provides data on tailgating hotspots to support employers’ policies and stop breaches. Image courtesy of Alcatraz AI
Find out more at www.alcatraz.ai
Altronix
Powers Access for Multiple Doors
The Altronix Trove Access and Power Solution, an angled bracket system, accommodates up to 36 doors or 24 powered doors without the need for mounting hardware on the enclosure door. The bracket system also includes an optional battery cabinet which mounts directly under the enclosure. The Trove solution with removable backplanes aims to simplify board layout and wire management, allowing installers to configure and test systems prior to on-site installation. Image courtesy of Altronix
Find out more at www.altronix.com
ASSA ABLOY
Protects Data and Security Equipment

The HES KS Series Server Cabinet Locks from ASSA ABLOY work with existing access control systems to help protect server racks from intrusion. Four cabinet locks aim to secure data and other assets in various ways: the KS200/210 model is an integrated wired swing handle server cabinet lock; the KS200 utilizes a Wiegand interface; the KS210 uses native RS-485 OSDP communication; and the KS-M is a mechanical server cabinet lock and can be installed on most cam-activated server cabinet doors. Image courtesy of ASSA ABLOY
Find out more at www.hesinnovations.com
Boon Edam
Keeps Intruders Out and Users Safe
The Tourlock 180 and Tourlock 120 revolving door models have been relaunched by Boon Edam. Both models are compliant with the European Standard EN 17352, which specifies requirements and test methods for pedestrian entrance control equipment. These doors have been updated to provide security protection through anti-tailgating and piggybacking functions. The Tourlock 180 and Tourlock 120 are equipped with an emergency stop button; buffers to protect user hands and feet while using the technology; instructional safety information; and features that help avoid entrapment. Image courtesy of Boon Edam
Find out more at www.boonedam.com
Bosch
Monitors Traffic in Various Lighting Conditions
Bosch’s Traffic Detector software aims to detect, classify and locate vehicles in busy traffic situations under challenging lighting conditions. The program uses AI to help improve detection capabilities in congested scenes and more accurately count multiple vehicle subclasses. The software also has the ability to count people. Traffic Detector software has been deployed on Bosch’s Inteox fixed and moving object classification (OC) camera models. The program’s AI algorithms are trained to ignore potential disruptions caused by vehicle headlights or shadows, extreme weather and sun reflections. Image courtesy of Bosch
Find out more at www.boschsecurity.com
DITEK
Helps Protect Security Technology from Electrical Surges

The DTK-VM2 and DTK-VM2T Series’ four-, eight- and 24-channel enclosure options accept modules designed to protect any combination of signaling, data and low voltage power circuits from 5V up to 130V. All of the enclosures in the series accept modules equipped with either RJ45 or screw terminal connections, and all options feature single-point grounding. This solution aims to simplify surge protection for all kinds of critical electronic systems, including surveillance, access control, fire, fuel dispensing, point-of-sale, communications, industrial controls and audio. Image courtesy of DITEK
Find out more at www.diteksurgeprotection.com
Dortronics
Helps Customize Access Control Options

The 48900 PLC Interlock Controller helps implement door interlock systems with up to nine doors. The fully integrated, single-board solution aims to provide installers with complete control of all operating and configuration options without the need and expense of complex software. The 48900 Series Controller integrates with access control systems utilizing dry contacts. The unit can also supply outputs for traffic lights, door violation alarms and three individual timing sequences for propped door time, emergency override unlock and request-to-exit unlock time. Image courtesy of Dortronics
Find out more at www.dortronics.com
Genetec
Helps Migrate Surveillance Data to the Cloud
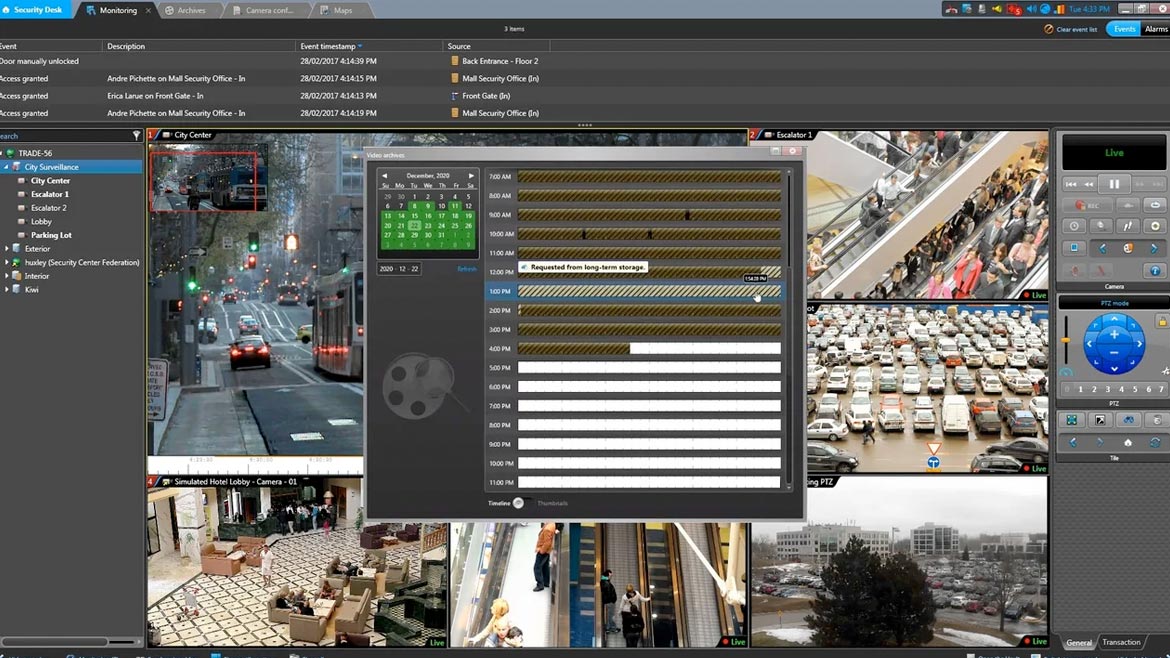
The 5.10 version of Genetec’s Security Center brings enterprise video surveillance users options to facilitate their migration to the cloud as well as support flexible hybrid-cloud architectures. Security Center Omnicast — the video management system of Security Center — can store video archives in the cloud and on-premises. Ingested video blocks are encrypted on-premises and then moved to the cloud using encrypted communications channels. Security Center 5.10 uses a no-code solution to connect external data sources. Users can define record types and consume data from a variety of sources, including KML, JSON and CSV documents or set up a REST application listening point to which these external services can push records. Image courtesy of Genetec
Find out more at www.genetec.com
Hanwha Techwin
Initiates Touchless Intercom Calls
The TID-600R Network Intercom Station features a 2MP sensor with a wide dynamic range (WDR) and low light performance. The lens offers a 180-degree field of view while IR provides up to 16 feet of illumination from the station at night. The TID-600R’s touchless call system can allow users to present their palms within 6 inches of the station to initiate a call. With full support for session initiation protocol (SIP) 2.0, the station can integrate with a wide variety of video management systems, access control, SIP phones or private branch exchange (PBX) servers. Echo cancellation, noise reduction and a built-in tamper switch aim to improve user security posture. Image courtesy of Hanwha Techwin
Find out more at www.hanwhasecurity.com
Louroe Electronics
Analyzes Audio to Detect Security Threats

The DigiFact 830 is a two-way, ceiling-mounted 6.5-inch IP Network speaker microphone. It uses networked audio monitoring technologies to analyze and stream bi-directional audio. Integrating into the Louroe Microphone Application Platform (LMAP), this WDR audio device aims to capture a broad frequency response capable of picking up low and high-frequency audio. The DigiFact 830 is capable of running an analytical application that detects and processes sounds of threats, including a pre-set decibel audible alarm, belligerent or aggressive voice signals, breaking glass, car alarms, gunshots and explosions. Image courtesy of Louroe Electronics
Find out more at www.louroe.com
Morse Watchmans
Manages and Tracks Key Activity
Morse Watchmans’ KeyWatcher Touch system is a key control and asset management solution for small to global enterprise organizations. The SmartKey system aims to enable the control and usage tracking of each key or key set. The KeyAnywhere technology allows users to withdraw and return keys securely to any KeyWatcher Touch system in an enterprise via a 7-inch touchscreen. Key administrators can locate which KeyWatcher Touch contains a specific key or determine who has it out with the KeyFind feature. The solution can generate PDF reports of key activity for further analysis. Image courtesy of Morse Watchmans
Find out more at www.morsewatchmans.com
Panasonic i-PRO
Surveils Areas With AI-Enhanced Video and Sound

The i-PRO S-series line of network cameras comes with a built-in AI processor that transforms the camera into an edge-computing device to help improve surveillance operations and offer the ability to select and install third-party applications without a cloud- or server-based connection. Surveillance videos captured by the cameras are encoded as H.265 files, aiming to conserve network bandwidth and server storage capacities. Sound classification technology can allow users to set alarms for targeted sounds, such as gunshots, yelling, vehicle horns and glass breaking using an external microphone. The i-PRO S-series is compatible with i-PRO’s multi AI system, a search function that finds people or vehicles through video management software. Image courtesy of Panasonic i-PRO
Find out more at www.i-pro.com
ProdataKey
Manages Access With Mobile Credentialing
ProdataKey’s (PDK) Red Readers can support high-frequency smartcards, low-frequency communication and mobile credentialing. Red mobile credentials are issued from within the PDK software application, to allow users control over credential creation and distribution. The cloud-based access control solution can support multiple options for identity credentials, allowing security teams to fit the technology into their organization. Image courtesy of ProdataKey
Find out more at www.prodatakey.com
Sielox
Combines Access Control With IoT Platforms
The Sielox 2700 Access Controller aims to deliver intelligence at the edge with onboard processing. Scalable to accommodate up to 34 doors, the 2700 Access Controller is a control panel featuring an embedded Linux platform. The panel aims to execute critical access functions with on-board database backup to perform independently when necessary. Image courtesy of Sielox
Find out more at www.sielox.com
Teledyne FLIR
Uses Thermal Imaging to Protect Perimeters

The Triton FH-Series are ruggedized, multispectral fixed cameras that integrate thermal imaging to help identify intruders in harsh perimeter security settings. The cameras include convolutional neural network (CNN)-based video analytics for both thermal and visible spectrums, which aim to minimize false alarms and aid in geo-locating threats. The on-board scheduling tool allows users to select the type of analytics employed to make detections based on time of day, business hours and seasonality. Radiometric versions of the Triton FH-Series can be used for early fire detection applications. Image courtesy of Teledyne FLIR
Find out more at www.flir.com
Vector Flow
Monitors Physical Security Devices

Vector Flow’s Security Operations Center (SOC) Automation Suite includes three key AI-driven modules: SOC Alarm Reduction, SOC System Health and Predictive Maintenance and SOC Governance. The SOC Automation Suite can monitor thousands of connected physical security devices automatically and detect failed devices or early warning signs of device failure. With the SOC Governance module, security management can monitor and assess the organization’s current security state and analyze the performance and outcomes for each SOC operator with metrics such as unacknowledged alarms, mean-time-to-acknowledge (MTTA), critical alarms by site and more. Image courtesy of Vector Flow
Find out more at www.vectorflow.com
Viakoo
Automates IoT Device Certificate Management
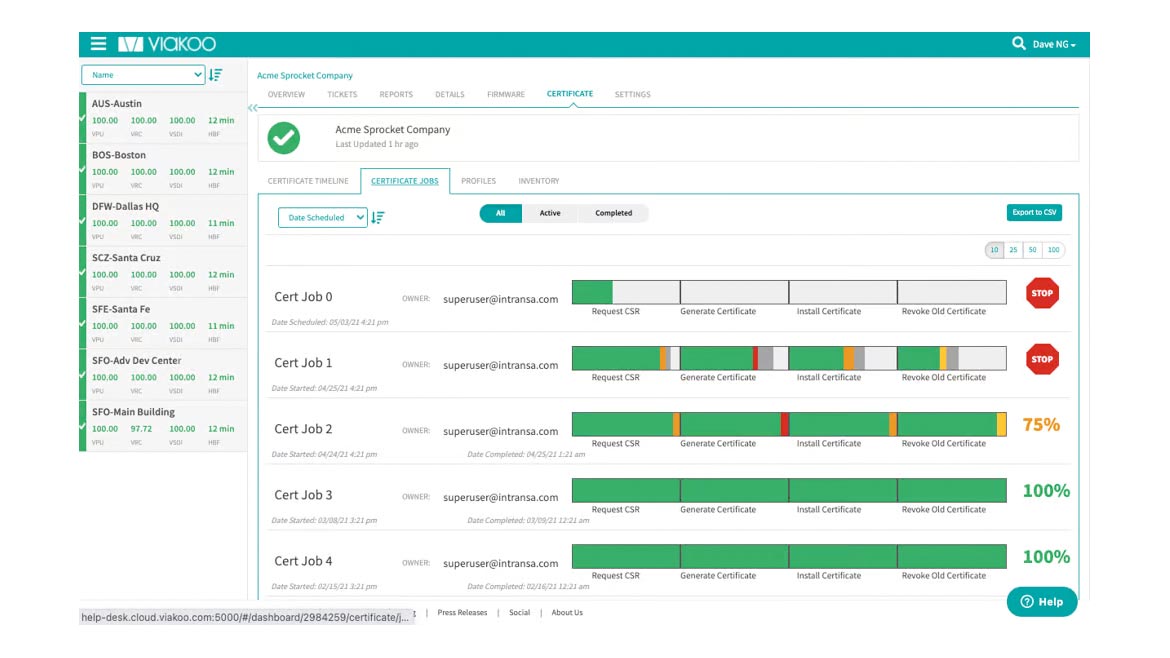
Viakoo’s Device Certificate Manager (DCM) helps automate the process of provisioning, refreshing and revoking IoT device certificates such as 802.1x, TLS/SSL, OPC-UA and others. DCM provides information on IoT devices, including certificate status and automates actions to maintain them. A chain-of-custody process is incorporated to ensure device certificates cannot be modified or compromised. Image courtesy of Viakoo
Find out more at www.viakoo.com
viisights
Integrates Video Surveillance With Behavior Analytics
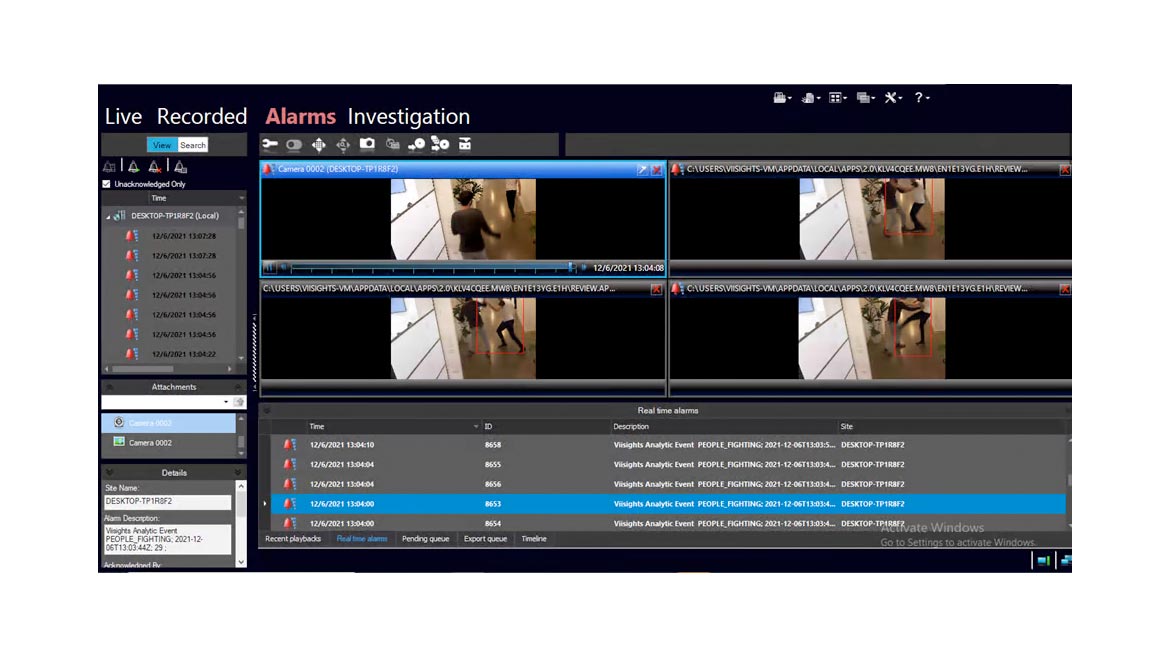
AI-powered video provider viisights has integrated its wise behavior recognition video analytics with Cognyte’s Symphia analytics solutions to help predict violent activity, suspicious behavior, crowd behavior, traffic monitoring, environment and personal safety and help prevent events from happening or escalating. With the integration of the security solutions, security professionals can access real-time insights for situational awareness, incident management, emergency response and investigations. Image courtesy of viisights
Find out more at www.viisights.com







